Goal
Deploy EKS cluster in two accounts and provide access to access the cross EKS/K8s/AWS cluster.
Scenario#1
Pre-Requisites
You must be having two AWS account to create infrastructure resources on AWS cloud.
Deployment
Perform below steps to deploy the above said architecture to achieve the below scenarios
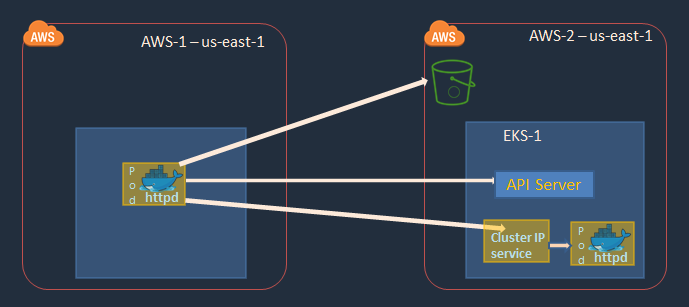
- Access S3 Bucket running in AWS-2 account from the Pod running in the AWS-1 account EKS cluster.
- Access the AWS-2 EKS API endpoint from the Pod running in the AWS-1 account EKS cluster.
- Access the Cluster IP service running in the AWS-2 EKS cluster from the Pod running in the AWS-1 account EKS cluster.
AWS-1
- Deploy EKS cluster in the us-east-1 region private subnets with any cluster
- configuration that you choose! we just need EKS cluster running with simple configuration!
- Write a Dockerfile keeping below packages installed to build the image and publish the image to your preferred Image Registry like ECR, DockerHub
- Base Image: Amazonlinux
- Install kubectl
- Install aws cli
- Install telnet
- Install apache HTTP web server
- ENTRPOINT to start the web server
- Deploy the application using the container image created in the previous step and also create a Cluster IP service to access the application.
- Ensure the application Pod is running fine and verify the kubectl, aws cli commands are working fine.
AWS-2
- Deploy EKS cluster in the us-east-1 region private subnets with any cluster configuration that you choose! we just need EKS cluster running with simple configuration!
- Deploy the application using the container image created in the previous steps.
- Create S3 bucket with any name that you choose and upload simple object file.
Scenario #1
Access S3 Bucket running in AWS-2 account from the Pod running in the AWS-1 account EKS cluster.
- Create IAM role in the AWS-2 account and grant the access to S3 bucket that you created previously.
- Create IAM Role in AWS-1 account to assume the IAM role in the AWS-2 account created in the previous step
- Create a Service Account in the AWS-1 EKS cluster
- Grant Service Account to assume the AWS-1 IAM Role.
- Attach the Service Account to the Pod running in the AWS-1 EKS cluster – Probably you need to modify deployment manifest and re-deploy.
- Execute “aws s3 ls” command in the AWS-1 EKS running Pod to ensure that the cross AWS account S3 bucket is accessible from Pod.
Scenario # 2
Access the AWS-2 EKS API endpoint from the Pod running in the AWS-1 account EKS cluster.
- Create IAM role in the AWS-2 account and grant the access toAWS-2 EKS cluster that you created previously.
- Update K8s RBAC to allow the access to IAM role created in the previous step.
- Create IAM Role in AWS-1 account to assume the IAM role in the AWS-2 account created in the previous step
- Create a Service Account in the AWS-1 EKS cluster
- Grant Service Account to assume the AWS-1 IAM Role.
- Attach the Service Account to the Pod running in the AWS-1 EKS cluster – Probably you need to modify deployment manifest and re-deploy.
- Execute “kubectl get pods” command in the AWS-1 EKS running Pod to ensure that the cross account EKS API Server accessible from Pod.
Scenario #3
Access the Cluster IP service running in the AWS-2 EKS cluster from the Pod running in the AWS-1 account EKS cluster.
- Deploy Cluster IP service in the AWS-2 EKS cluster to access the application running in the AWS-2 EKS cluster
- Create Ingress object to access the Cluster IP service using Internal Load Balancer.
- Setup Peering/Transit Gateway to access the Internal LB endpoint from the AWS-1 account.
- Run curl command on AWS-1 EKS running pod to check the application running in the AWS-2 EKS cluster pod.
Good Luck!