Table of Contents
Goal
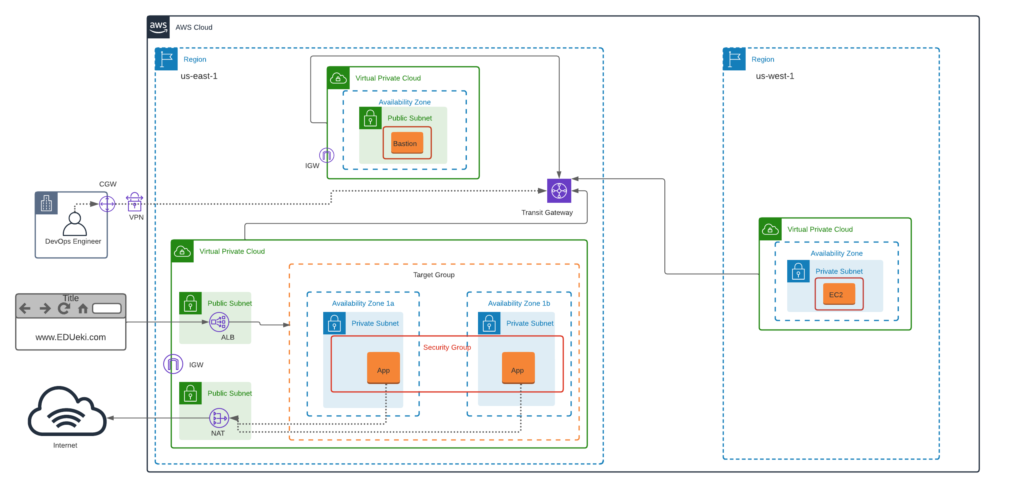
Deploy a Modular, Highly Available AWS VPC Architecture with Transit Gateway
Pre-Requisites
- You must be having an AWS account to create infrastructure resources on AWS cloud.
- Source Code
VPC Deployment
Note that You can use any subnet CIDR that you can plan based on the VPC CIDR to meet the requirements with optional tags and possible resource sizes to all AWS resources.
us-east-1
- Build VPC network ( 192.168.0.0/16 ) for Bastion Host deployment as per the architecture shown above in us-east-1.
- Build VPC network ( 172.32.0.0/16 ) for deploying Highly Available application servers as per the architecture shown above in us-east-1.
- Create NAT Gateway in Public Subnet and update Route Table associated to Private Subnet accordingly to route the default traffic to NAT for outbound internet connection.
- Create Internet Gateway for both VPC in us-east-1 and update Route Table associate to Public Subnet accordingly to route the default traffic to IGW for inbound/outbound internet connection.
- Create Security Group for bastion host allowing port 22 from public.
- Deploy Bastion Host EC2 instance in the Public Subnet with EIP associated.
- Create Security Group for app servers allowing port 22 from only Bastion Host and allowing port 80 from Public.
- Login to both app servers and Install Apache web server application and ensure the app is listening on port 80.
- Deploy HTML source code to apache web servers [Optional step]
- Create Target Group and associate both App servers as Targets.
- Create Application Load balancer in Public Subnet and configure Listener rules to listen on port 80 and forward the traffic to Target Group.
us-west-1
- Build VPC network ( 172.35.0.0/16 ) for deploying application servers as per the architecture shown above in us-west-1.
Transit Gateway
- Create Transit Gateway and associate three VPCs to the Transit Gateway for private communication.
Explore
- VPN is the Virtual Private Tunneling that can be created between Corporate Physical Datacenter network to AWS network to access the AWS Private IPs directly from your Corporate network.
- VPN can be setup using CGW [Customer Gateway] and VPG [Virtual Private gateway]. But its not feasible to implement this without a CGW, Hence just explore the concepts how it can be established to access private IPs directly from local corporate datacenter. Follow the LINK for more details.
NOTE: Private Tunneling can also be configured using AWS Direct Connect. Follow the LINK to know more about this setup.
Validation
- As DevOps Engineer login to Private Instances of both regions via Bastion Host.
- Browse web application from public internet browser using ALB name and verify that page loaded.[You can not access the website using www.EDUeki.com as shown in the architecture for reference, So, use ALB name for accessing the site.]
Solution:
Will be updated Soon…..
© Edwiki Trainings – Click HERE If you are interested to learn more on Cloud & DevOps stack.






