Here in this Article I am explaining how to configure AWS IAM access to configure AWS provider in Terraform.
Below are the different methods to configure AWS provider:
- Static Credentials
- Environment Variables
- Shared credentials
- EC2 Role
Pre-Requisites
Create IAM user and IAM role with the correct IAM policy attached to the user or role to manage AWS resources.
- Create IAM User
- Create IAM Role
- EC2 Instance attached with IAM Role
Note: AWS generates access key and secret key while creating user, store the keys securely.
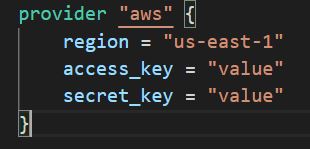
Static Credentials
Below Provider block showing the basic syntax to configure AWS provider with Static Credentials in ‘us-east-1’ region. Replace the access_key and secret_key values with the actual keys that were downloaded at the time of creating the AWS User in the Pre-Requisites step.
Environment Variables
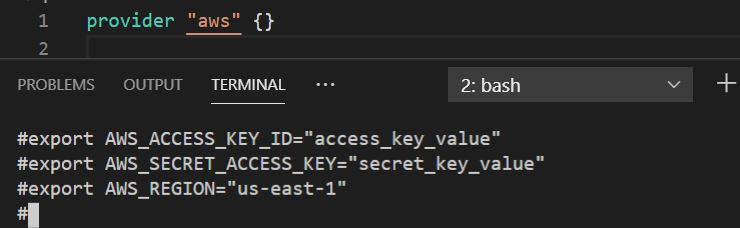
Below Provider block showing the basic syntax to configure AWS provider using Environment Variables in ‘us-east-1’ region.
![]()
Credentials can be provided by using the AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY environment variables. The region can be set using the AWS_REGION environment variable.
Replace the access_key and secret_key values with the actual keys that were downloaded at the time of creating the AWS User in the Pre-Requisites step.
Shared Credentials
Below Provider block showing the basic syntax to configure AWS provider using Shared Credentials in ‘us-east-1’ region. Note that, AWS CLI must be installed to working with the local shared credentials file.
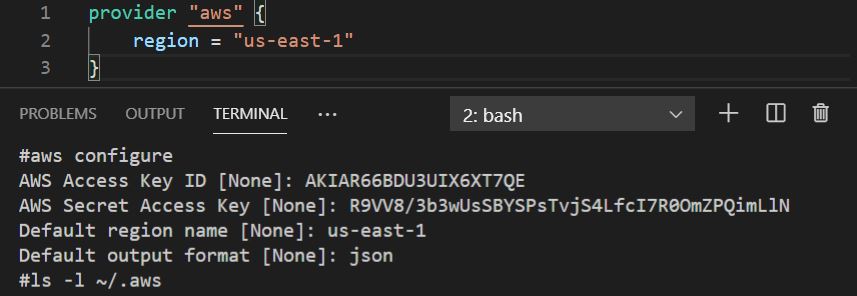
Credentials configured using “aws configure” command by default storing the credentials as default profile in local shared configuration file located in ~/.aws/config and ~/.aws/credentials on Linux and macOS, and “%USERPROFILE%\.aws\config” and “%USERPROFILE%\.aws\credentials” on Windows.
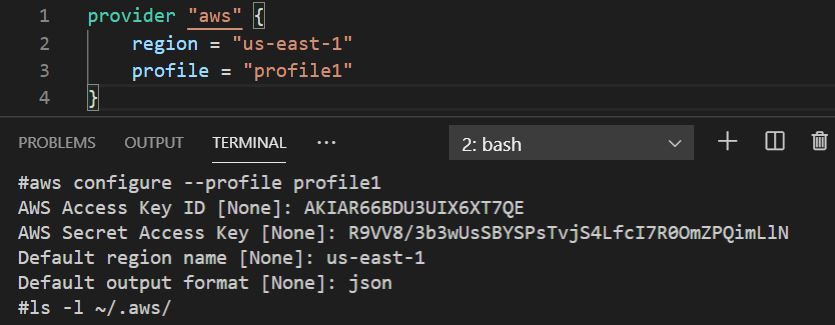
Follow below steps to store in custom profile name “profile1” using “#aws configure –profile profile1” command
EC2 Role
If you are deploying the resources from EC2 then, Credentials are not required to supply. Attach a IAM Role to the EC2 with required IAM policies.
Below Provider block showing the basic syntax to configure AWS provider using IAM Role attached the EC2 in ‘us-east-1’ region.
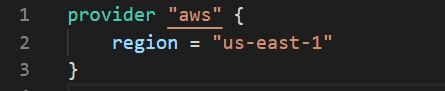
Terraform assumes the IAM Role that was attached to the EC2 instance to gain the permissions to deploy resources on AWS cloud.
Comment below which method you use the most while you deploying the AWS resources using Terraform IaC. Good Luck!
© Edwiki Trainings – Click HERE If you are interested to learn more on Cloud & DevOps stack.


